Privacy week: Surf anonymously with the TOR Browser.
Feb 04The TOR network, better known as “The Onion Router” network is mesh of “endpoints” all over the world, interconnected by a encrypted connections. Much like a network of Wormholes, traffic can go in on one end and leave the TOR network in a completely different (and random location) to “go on the internet.” I know some of you might be wondering what this is for, so , imagine being in China and wanting to watch something on Youtube. The Chinese government does not only block a lot of “Western” websites, it also keeps track of the traffic its citizens generate. Enter the TOR network. Using this network our Chinese Youtube enthousiasts sends his traffic through the TOR network. The actual request “emerges” onto the internet in some random country (where Youtube is not blocked) AND its encrypted along the way. So he gets to watch his favourite catvideo AND the government does not have a clue what he is doing.
So how can this work for you ? Whenever you are on a public hotspot or on a network you do not trust, you can use the TOR browser. Your browsing behaviour will not only be completely opaque to whoever is trying to watch your movement on that network , it ALSO will circumvent URL and content restrictions.. because if they look at your traffic .. they will only see an encrypted tunnel between you and whatever TOR endpoint you are connected to. Nobody can sniff you, Nobody can block you. Eat that Starbucks Script-kiddy !
The TOR browser is a “mutated version of Firefox” that lets you surf DIRECTLY on the TOR network. It is available for Windows, Linux and the Mac and is COMPLETELY PORTABLE (you don’t even have to install it). So carry it around with you on your USB stick and be absolutely sure that, next time you are logging in on that Wifi network in the Hotel Lobby .. nobody can “follow along”.
Download the TOR BROWSER BUNDLE here.
Related Posts
Setting up your own SSH proxy on Windows.
Jan 22Free wifi is great. It’s like finding an oasis in the middle of the desert that gives you the ability to quench your digital thirst before you wade into the offline sahara once again. But “Open and Free” wifi comes at a price. Being a shared network medium, it means that all traffic on the wireless network is visible to all users on that network , should they care to take a peak.
With networking tools like “Wireshark” it is fairly easy sniff traffic on an open wifi network and intercept all kinds of unencrypted traffic. That traffic can consist of what URL’s you surf to to what passwords you use (if you have an unsecured connection) .. They are all there for anyone to sniff, download and analyse.
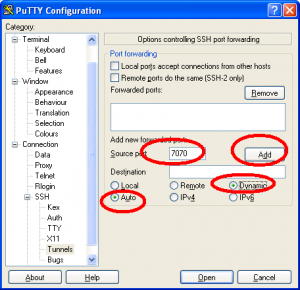
To keep your browser traffic private all you need to do is encrypt it. One of the ways to do this is of course use https connections where you can, but if that is not possible there are alternatives. You can set up your own SSH proxy server. This means you will be creating an encrypted tunnel from your laptop, TROUGH the internet, to your home server. Once there (behind the security of your own firewall) your traffic heads for the internet. Its like surfing at home, but you are in fact ‘away from home’.
The only thing you need are :
– Access over SSH to a linux server. ( Check our our tutorial on how to set this up)
– A copy of Firefox.
Setting it up is quite easy , and we will probably do a screencast on the issue in season 8 of our podcast, but instead of boring you with a lot of text , we are going to point you to the excellent podcast episode Kurtis Adkins did for Hacker Public Radio on the topic. Take 20 minutes and listen carefully. When you are done (and have the ingredients above) you will be able to secure your webtraffic from anyone who wants to snoop around. (Hackers, scriptkiddies or nosy sysadmins)
Link : Curtis Adkins on : Setting up and using SSH and SOCKS (Hacker public Radio ep 1422)