Free wifi is great. It’s like finding an oasis in the middle of the desert that gives you the ability to quench your digital thirst before you wade into the offline sahara once again. But “Open and Free” wifi comes at a price. Being a shared network medium, it means that all traffic on the wireless network is visible to all users on that network , should they care to take a peak.
With networking tools like “Wireshark” it is fairly easy sniff traffic on an open wifi network and intercept all kinds of unencrypted traffic. That traffic can consist of what URL’s you surf to to what passwords you use (if you have an unsecured connection) .. They are all there for anyone to sniff, download and analyse.
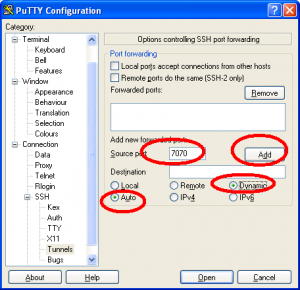
To keep your browser traffic private all you need to do is encrypt it. One of the ways to do this is of course use https connections where you can, but if that is not possible there are alternatives. You can set up your own SSH proxy server. This means you will be creating an encrypted tunnel from your laptop, TROUGH the internet, to your home server. Once there (behind the security of your own firewall) your traffic heads for the internet. Its like surfing at home, but you are in fact ‘away from home’.
The only thing you need are :
– Access over SSH to a linux server. ( Check our our tutorial on how to set this up)
– A copy of Firefox.
Setting it up is quite easy , and we will probably do a screencast on the issue in season 8 of our podcast, but instead of boring you with a lot of text , we are going to point you to the excellent podcast episode Kurtis Adkins did for Hacker Public Radio on the topic. Take 20 minutes and listen carefully. When you are done (and have the ingredients above) you will be able to secure your webtraffic from anyone who wants to snoop around. (Hackers, scriptkiddies or nosy sysadmins)
Link : Curtis Adkins on : Setting up and using SSH and SOCKS (Hacker public Radio ep 1422)