Today on our Google Hacking week, we continue to use the Google search engine as a source for interesting information. In our previous posts we talked about finding and downloading certain kinds of files but today we are on the lookout for “juicy devices”.
The theory is quite simple : Most appliances like webcams, routers, copiers and more have web interfaces. A lot of different applications and services can also be controlled by a web interface. It’s easy and convenient when you can use the browser on your computer to configure and watch your webcam or change settings on your router while on your local lan. But what if those devices are hooked up directly to the internet ?
Any device that gets connected directly to the internet is at some point scanned and indexed by Google and if you enter the right search term you will be able to find it. The way we are looking for those devices and services today is by using the INURL option. Some web interfaces (to your router or webcam) have a very specific way their URL looks. By searching for those specific url types with the INURL option.. you can find some very cool stuff. If people have done their homework most of these services will be blocked by a unique login or password. But some people just use the default password … or even none at all.
Let us take you an a walk through the net with some very specific INURL Google Dorks.
- inurl:ViewerFrame?Mode=
- This one will get you some interesting webcams (some you can even control with your mouse). Look around and see if you can find the Giraffe Cam.
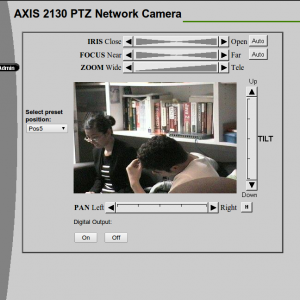
- inurl:view/view.shtml
- More network camera’s here. This one is in some dorm/college. You can control the zoom and the direction of the camera.
- inurl:”:10000″ intext:”webmin”
- Remember we talked about WEBMIN ? This will give you a list of all webmin servers connected directly to the internet. most of them are protected by a password (we hope) .. but common usernames like ROOT and some generic passwords might get you in.
- inurl:”32400/web/index.html#!/dashboard”
- This will get you a list of PLEX media servers where people can store music and movies to watch on any device (even across the internet). Most of them are locked down with a login/password. Some of them … are not. Happy streaming.
So you see : there are quite a few webservices out there that are inadvertently open to the indexing power of Google. Some clever searching and you can find them.
We close off by going by to our camera in the student dorm. Where is this ? A simple ping of the url gives us the following IP : 138.25.6.37 and by going to Whereisthisip.net we find out that its Sydney Australia. Its THAT simple.
Puzzling information together.
This might all look like fun and games, but badly secured devices are dangerous. Whether you have weirdo’s peeking through your accidentally-publicly-connected Ip camera, or random people printing out documents on your www-connected printer.. its never good. Using the Domain name, the IP and the registration information of the domain people can quickly find out where and even WHO you are. If you skip good security and don’t use passwords (or default passwords) .. it does not bode well for you. Hackers even use the INURL search to find specific webservers/services with vulnerabilities. All they then need to do is run some code to take advantage of the exploit .. and they are in. Hackers don’t NEED to search for your open Webmin server with the buggy (and vulnerable) version of the http code .. Google did it for them.